Resource Center
-

A Day at MSSP Alert Live
Late last week, while working with my team on our continued search for a Next Gen Security Information and Event Management (SIEM), Security Orchestration, Automation, and Response (SOAR), and User…
-
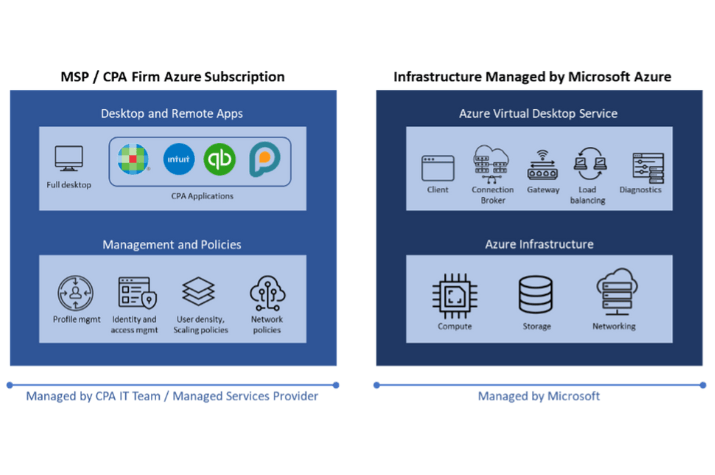
How Azure Virtual Desktop is Redefining Collaboration in the CPA Vertical
As a Cloud Managed Services Provider (MSP) focused on the CPA profession, we work extensively with CPA firms to manage their IT infrastructure and deliver a virtual desktop solution that…
-

Takeaways from the Boomer Consulting BTC Summit 2022
Wow, what a week. The Netgain Fintech team attended a well-organized and executed Boomer Consulting’s BTC Summit 2022 event at a fantastic new location, the Loew’s Hotel in Kansas City’s…
-

A Primer on Vulnerability Management
You are a business that stores data on your organization’s network and wants to keep the network as secure as possible. Protecting your business assets has become a complex challenge…
-
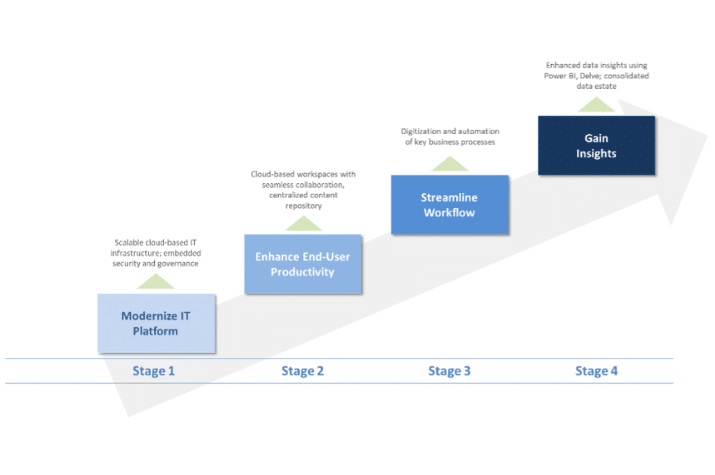
CPA Firm of the Future – Is your Infrastructure Ready? 3 Things to Consider
1. Tech intensity is key for firms to adapt and thrive CPA firms today are navigating several common challenges as they seek to expand their advisory services through organic growth,…
-

Three Tips on Why Multi-Factor Authentication is Critical to Data Security
Cybercrime is rife in 2022. Kaspersky released a new report revealing a growing number of cyberattacks on small businesses so far in 2022. Researchers compared the period between January and April 2022…
-

Comparing Remote Desktop Requirements to Azure Virtual Desktop
5 Top Things To Consider When Comparing RDS to AVD For Your Organization Many companies are still navigating or attempting to upgrade their capabilities for a hybrid work environment. There…
-

AICPA Engage 2022 Conference – An Overview from a Technology Provider’s Perspective
It was great to be back in person at AICPA’s Engage Conference last week in Las Vegas! As a provider to the CPA profession, I was excited to see the…
-

2022 RSA Conference – 3 Key Takeaways
According to this article by CRN about this year’s RSA Security Conference, “cybersecurity is now in ‘fast-forward’ mode where attendees are almost in awe at the transformation of the industry…
-
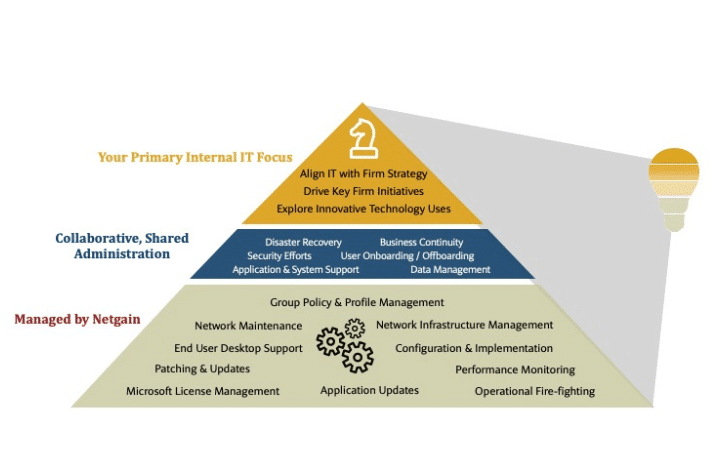
The 80/20 Rule: Balancing Innovation with Operational Execution
Traditional client satisfaction metrics (CSAT, NPS) provide useful insights into value created by managed services providers (MSP), but they are not the most important metric. Instead, the question that we…
-

Netgain Technology Named on ChannelE2E Top 100 Vertical Market MSPs: 2022 Edition
Seventh-Annual List Reveals Leading MSPs In Healthcare, Legal, Government, Financial Services & More April 25, 2022 – Minnetonka, MN: Netgain Technology LLC, an industry-aligned cloud solutions provider focused on serving…
-
Security Lesson #7: The Essentials of Implementing Effective Perimeter Security
As I highlighted in my first post, no company or government agency is immune to cyberattacks, and these attacks are a growing threat to every organization. To protect against these attacks, you need…